A word of Caution – This Blog post on Deep Web is just for information purpose. DO NOT misuse it’s information in a wrong way. DO NOT ATTEMPT to test or access the websites/links given here unless you are acquainted with the basics. Accessing the websites/links for fun purposes might open you up for cyber attacks invading your privacy.
We as INDIANS are too confident that we are on the brink of seeing another Technology boom in form of Artificial Intelligence/Machine Learning/Big Data. We are already on #2 position in the list of countries with highest number of Internet users. It won’t be wrong to state that if the progress continues at this pace, we would be soon on #1 ranking surpassing CHINA.
Our confidence is amazing, but food for thought is – Are we really gonna ever make it to #1 position?. You might wonder why do I ask this question. The answer is simply: we might call ourselves heavy internet users, but are we using it to its full extent? NO we are NOT. Its’ because we have no idea the extent to which the internet has widespread.
DEEP WEB / THE DARKNET: Hidden part of web which a normal user can’t access
Various surveys leads to different theories. One of the core theories indicate that among the 7.9 Zettabytes of data available online, we are using just 4% available on search engines like Google, Bing etc. The rest 96% (90% + 4%) is protected by high-security passwords hidden behind paywalls or can be accessed via special tools or software’s.
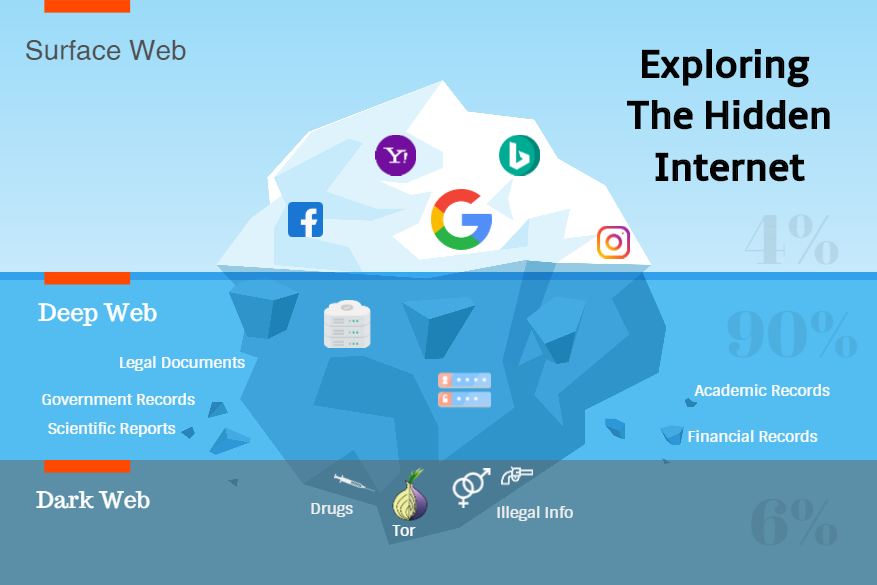
The Deep Web is that part of web where all illicit activities take place. It’s that underground area where hackers, pedophiles, gangsters and even terrorists come together to perform their business. The business involves just showcasing a sample of goods and services and getting their work done.
Levels of Deep Web or Dark Net
The 4% data we access is often termed as Surface Web. However, DEEP WEB on a contrary isn’t just one single layer, but amalgamation of multiple layers. Every layer has its own set of tools and software’s commonly used by dark-net users.

The image is self-explanatory, isn’t it? We at most reach out till Level-3, all thanks to P2P software’s like Bit Torrent to download pirated content. However, the last two levels i.e., Level 4 and Level 5 are areas which you must visit with utmost caution unless you wish to endanger your security. Making yourself prone to cyber attack on the pretext of having fun isn’t acceptable.
Deep Web Market – What All Can You Purchase?
While I was busy researching on Deep web, I often came across one major saying that:
Anything/Everything that You Can Imagine Becomes Available on DEEP WEB
As the business market of DarkNet is rich and prone to unaccountable risks, covering every item is beyond the scope of this blog post. However, let me jot down few items which you might find on DarkNet websites quite easily:
DRUGS
DarkNet is an open market to both prescribed and illegal drugs. You can find any and all sorts of cocaine, heroin, designer drugs here that has its own adverse impact on the brain power of a normal human being. Few sellers post images of their products online rendering them as legal and 99% pure which worsens the situation.
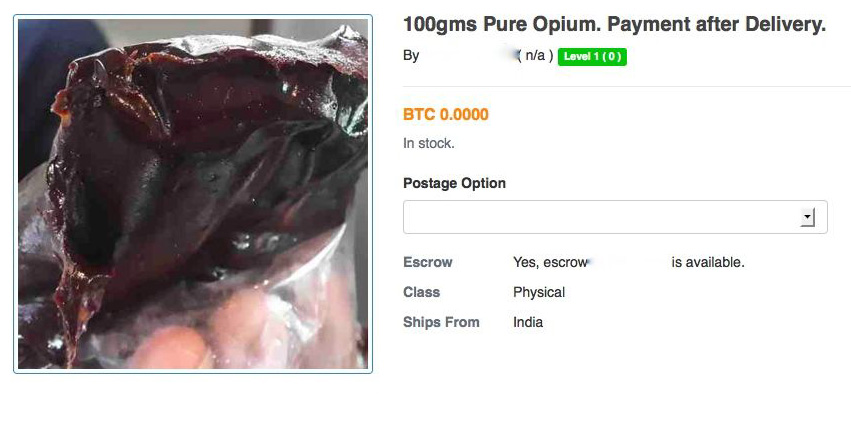
To showcase their products as more authentic, some sellers even attach verified documents with the products. You got to rely on the word-of-mouth as you have no means to verify the documents. Feedback of other users is equally important.
FORGED DOCUMENTS
Forgery is defined as the practice of making a duplicate/fake copy of any document illegally. The forging of official documents like Driving Licenses, Government. ID’s, Immigration Certificates or citizenship papers of a country are more dangerous than purchase of a drug.
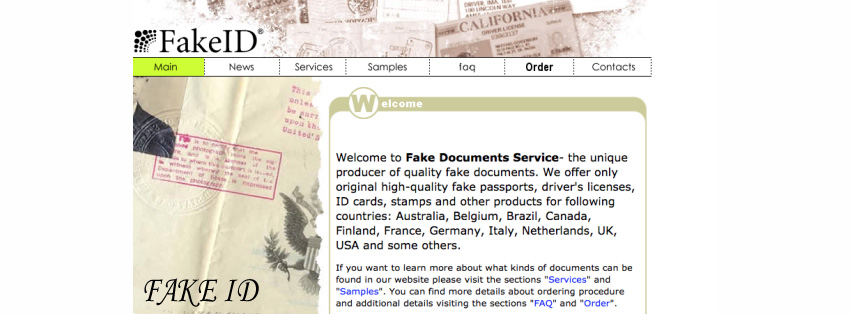
A recent study claims that you can easily obtain a U.S. driving license for $200 while U.S./UK passports for just few thousand bucks. The rapid rise of cryptocurrency in the past 2 years have made us more prone to cyber attacks. Bitcoin transactions/ Credit card details/ PayPal accounts nothing is safe anymore. You can easily obtain information of more than 1000+ credit cards in this market or can stamp the details on blank parchments.
AMMUNITION, FIREARMS, EXPLOSIVES
Its no mere coincidence that Deep Web encompasses a plethora of options when we talk about firearms/ammunition or explosives. Cyber criminals leveraging technology can easily purchase these items in any variant on a single click of a button.
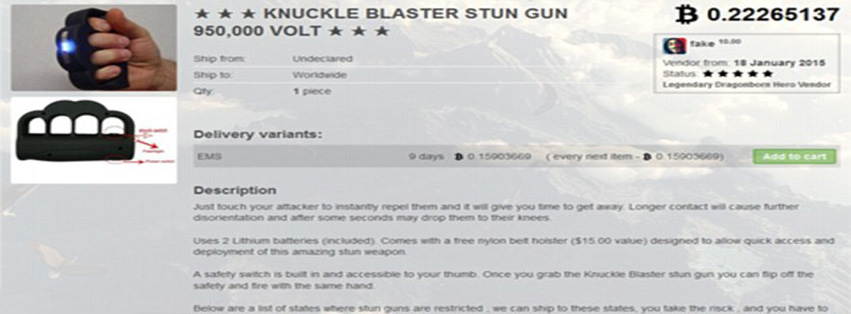
As per survey reports, vendors now ship their products by hiding them inside the toys or through shielded packages. The sole benefit of following such a practice is because X-ray machines don’t detect these packages. Other than toys, some suppliers are even seen using musical instruments like guitar, violin etc. to bypass security checks.
Guns are just a small segment of firearms. There is a whole army of weapons readily available for purchase on deep web market. Examples: quarter-sized piece of URANIUM or an EMP Pulse Generator.

One of the biggest examples ever known is of Silk Road shut down by FBI officials in 2013. If you have never heard about Silk Road, check out more information on Silk Road right here.
However, no matter what, a common man is still skeptical to buying arms on deep web. One major reason for such a behavior could be attributed to the availability of the product (in a single piece) in different weapon shows. It saves both the time and hassle of recombining individual components back together.
HIRING OF HACKERS
Yes, the heading might surprise you, but its a hard hitting reality. Deep Web does allow authorized and organized cyber-crime organizations to hire hackers for their illegal practices. A clear example: China’s Hidden Lynx group.

As reports claim, this group from CHINA involves 100+ professional hackers and thieves alike. Cyber criminals who bypassed security of tech giants like GOOGLE, ADOBE etc. too are a part of this group. In the span of last 6 years, this organization has been able to take down almost all major firms of U.S. region. You pay them and their experts would gladly provide you their services.
P.S. – Recently hackers broke into a Casino using fish-tank clearly showing how our reliance on Internet of Things has compromised our security.
Ways to Access Deep Web Directories
Reminder – DO NOT ATTEMPT to access these Websites or links being mentioned for reference purpose. It’s for your own good.
In today’s digitized world, everybody is a tech-geek having knowledge of any or every technical topic. We are living in a world which is quite rich in information and accessing the layers of deep web is like making yourself prone to mystical dangers. Check out this list of web links you can access while browsing deep web:
ANONYMOUS BROWSER
I know the term ‘Anonymous browser’ isn’t new to you, but not all of you would be aware of its literal sense. Being anonymous is the new trend. Everybody tries to surf through the internet on INCOGNITO (private browsing mode) on different browsers. Follow the link to know how to enable private mode on different browsers.
You must be wondering how can you browse all these websites/links to make an entry into deep web. The answer is using The Onion Router (TOR browser). Just like an onion has a number of layers, TOR browser also provides a gateway to the lower layers of Deep Web. Hiding the origin of the page request, it provides full security to the IP address of the end-user. Interested in knowing more about what is TOR and how it functions? Just follow the attached link and enlighten yourself more on the subject.
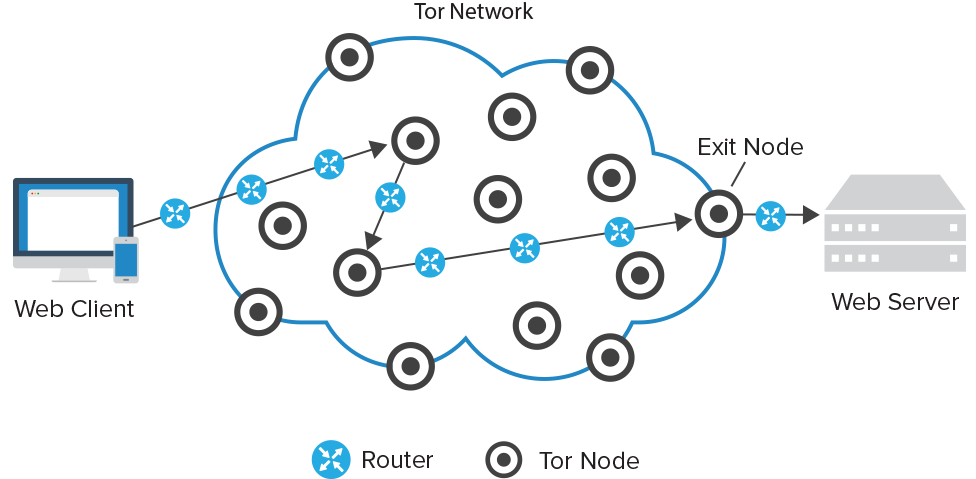
If you are using TOR, note that every webpage you access has a .onion suffix, indicating that you are not using a normal web browser. Post spoofing even law enforcement agencies are unable to track down a given or random IP address.
P.S:- You can’t access these TOR supportable webpages .onion suffix on your normal browser ever.
SECRET SEARCH ENGINES
I know you are thinking that I have gone crazy. But trust me guys, even Deep web has its specialized search engine just like GOOGLE. Its called GRAMS and both the search engines are similar in user interface and the overall look and feel. A normal hacker built GRAMS in mid-2014 and it won’t be a surprise if one can call GRAMS as the GOOGLE of DarkNet.
Various claims have different stories to unfold. One major revelation claims GRAMS allow the criminals to purchase genuine/good quality guns, all sorts of drugs and even steal bank account details of multi-users across the globe. As the UI of both search engines is similar, GRAMS too comes with an ‘I’m Feeling Lucky’ button with targeted ads permitting drug leaders to fight for clicks.
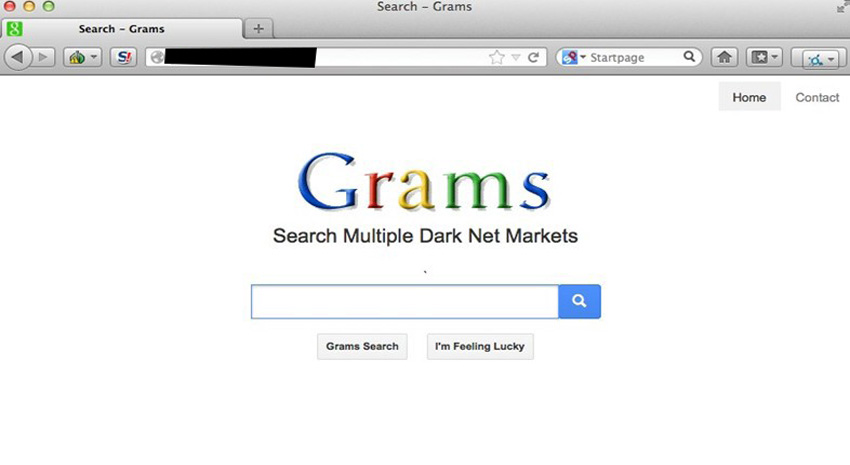
P.S.- GRAMS is not just a simple search engine. Its on the same path as GOOGLE and so is diversified to many other domains like:
- Gram words – similar to Google Ad-words
- Grams Flow – it gives easy access to hidden sites
Check out this Wikipedia article on GRAMS if you are interested in knowing more about it and the services it offers.
HIDDEN CHAT-ROOMS
When you get into a conversation with a random stranger online, you call it a chat. When you do this with multiple users at the same instance over a given network, you become a part of a chat-room. We as INDIANS are yet exploring this concept while globally people are too accustomed with the art of talking to random strangers online. You ought to be careful while indulging in a conversation with a random stranger and the same rule applies on Dark web chat-rooms.
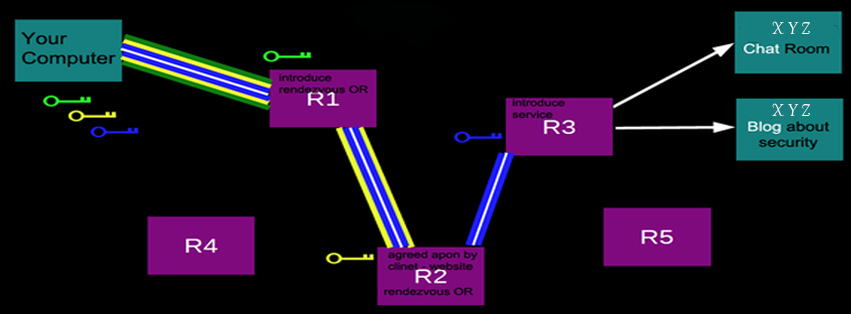
The chatrooms on Dark Net operate on the same principle as online criminals have to confirm the authenticity of their product(s) before beginning the transaction process. Few chatrooms seek authentication of newcomers from the admin(s) of that room failing which the user is denied full access. Few chat-rooms hide behind unlisted alphanumeric web addresses making it hard to track them thus requiring special tactics to open up.
VERDICT
Every coin has a flip-side. Hence, I won’t call Dark Web aka Dark Net to be completely bad. It has existed ever since the internet marked its presence. What matters is how we as individuals take it and use it. Though you can find a number of painkillers, sedatives online, yet pharmaceutical agents feel elated by sharing their products through Deep web. What they forget is that they are endangering their national security by following such illicit practices.
What more can be done to improve the situation? Its simple: every countries government needs to understand that privacy is not just keeping government surveillance at bay, it also involves keeping hackers and other cyber-thieves away from a person living a regular life. It’s vital to exercise caution as there is a very thin line between the two worlds i.e., virtual and real and one must not surpass it for the greater good.
Be Aware, Be Safe.
Pay heed to my warning again: This blog post is solely a guide to Deep Web and what all it covers. It in no manner encourages to start practicing illegal behavior.
Do share your feedback on the blogpost and let me know your thoughts on Deep Web in the comments section below.




“The name “”darknet”” is apropos. It just goes to show that people are not always “”good.”” There’s a whole lot of weirdness out there. That being said, I am glad that some people still hold themselves to a higher standard–but I also tend to think that this standard is a learned behavior, and not necessarily a given. At any rate, humans are lead astray rather easily…
Your article is very compelling and gives one plenty of food for thought. Up, useful, interesting.”
Regards
Deepweb Links
Hello,
I am glad you found my blog post compelling and it gave you something to think over.
Regards,
Admin
I did not even know this existed. Thanks for this information. I don’t think I’ll be visiting anytime soon, but it’s good to be informed! Voted up and shared.
Thanks, Mosen for your valuable feedback.
Regards,
Admin
Some of these just link to nonsensical conversations in Reddit!? Some are fucked up. But that torproject browser is bad news, surely it’s just encouraging paedos and sociopaths!
I will go through the links again Moses. Thank you for your update. Yes, indeed, practicing Dark Net definitely encourages paedos and sociopaths. . .